Latest Blog - PHP
One of the best languages for the web developers for developing dynamic websites is PHP. Developers love to use PHP because of the cool features that PHP provides the developers for best web application development.
As a PHP programmer, your first concern should is to make a web application that is secure and avoid any inadvertently that allow security holes to creep into a Web application.
To make the PHP website more secure, a PHP developer must understand the basic types of flaws any PHP applications tend to exhibit. To understand the blunders you must have the details about the common PHP programming mistakes that you might make and what are PHP security best practices.
Don’t worry this article is here to help you understand these mistake and some PHP security best practices to make your site supersonic secure.
New PHP installations use recent PHP releases, therefore, have the more secure code. But make sure your PHP application is installed on a good server with updated PHP version, not on the php.ini file.
To get through the problem of PHP configuration, the solution is to create a page that calls the phpinfo()- A function whose work is to list your php.ini variable and scan them for insecure settings.
The main thing that you have to keep in mind that you never allow public access to this profile as there is no compromise on the security of your website.
You have to keep in mind three setting for the configurations:
1: register_globals: The most important thing to keep in mind is to always disable them. If you are using a shared host and they don’t allow you to disable it, then it’s a high time to get a new host.
2: safe_mode: Enable this setting if your application opens the local files often. This setting is used to prevent the unauthorized access.
3: diable_functions: This has to be set in your php.ini file only. Disable it in your PHP installation. By doing so, it can prevent the harmful PHP code to be executed at run time.
The error called Data handling errors occurs when the local system’s file data is handled incorrectly and in an insecure manner. Never ever transmit your encrypted data with HTTP. Always use HTTPS that is more secure to transmit the secured data like credit card numbers and customer information.
To transmit the sensitive data to the user’s browser, always use SSL security or else a malicious eavesdropper on any router can easily catch the sensitive data and information out of the network.
Whenever you update your application using FTP, an insecure protocol, there is always a risk of data mishandling. Use SFTP or SCP over FTP to transmit your sensitive files to the server. That is a PHP security best practice.
Now, the most important tip is that you have to minimize the exposure to data handling flaws. This means minimizing the data and only keep the data that you use more often. The data that you don’t use for long time, just archive it! and store it offline.
Unvalidated input error – is the most common PHP vulnerability. Input refers to the input that users provide which should not be trusted. It can be a scam or can be malicious. Whatever user inputs, you have to validate to create a securing PHP web applications.
Restrict the user’s input, if some characters or symbols should not be the a part of user input, reject the input completely or just simply strip them out.
This the most important and noticeable PHP vulnerability that creates many problems with web development. Session ID contains the information of the user that is using the website and if the attacker could hijack the ID, all the info can be seen.
To prevent to protect the information of the user, a unique Session ID is assigned to each user. Not only this you also have to keep track the risks to migrate them over the internet.
Here is another tip to avoid PHP blunders:
To assign the Session ID, use the session_regenerate_id function. Use SSL secure connection if your site has article information.
One of the PHP vulnerability that must be treated with special concentration is Cross-site scripting or XSS, the subset of user validation. The blunder is that the malicious user embeds scripting commands — usually JavaScript- in the data that other user have to execute.
The solution is that that you have to filter these type of tags like <script>. This is will work when the content is first submitted to get reviewed.
Your PHP website has to be enough intelligent that it can easily report any error rather than showing it in the PHP web application. Make sure that the display_errors php.ini value is set to “0”, if not then all the errors that encounter during runtime will be displayed to the user’s browser. And any malicious user can easily take advantage of this errors and will take information about any entry point to the website.
The solution to avoid is to set the error_log ini variable to “1” to catch the frequent log errors. Or make your own custom error handling functions. To get further information read the PHP manual pages on error handling and learn about the set_error_handler() function.
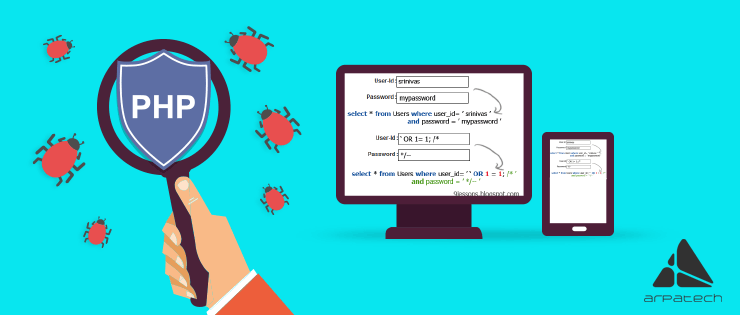
Another class of input validation flaws that affects the PHP security. They affect the database query and through this flaw, a malicious user can easily gain an entry point.
The solution is very simple, just escape all the dangerous characters that you see in the user-submitted values just like single quotes (‘).Check the user input using for the keywords “FROM”, “LIKE”, and “WHERE” in a case-insensitive fashion. Use addslashes() function in PHP language.
$username = addslashes($_POST["username"]); $password = addslashes($_POST["password"]);
PS: It depends on your PHP configuration.
Another magical feature that PHP provides is the magic_quotes_gpc php.ini variable and by setting it to Off means it will apply add slashes to all values submitted via GET, POST or cookies automatically.
This feature really helps full for the newbies in PHP programming and unexperienced developers, but the experienced developers always switch this feature off, but, if the software is installed on shared servers, where you can not edit the php.ini file, and this feature is on, check the status of magic_quotes_gpc by the following code.
if (get_magic_quotes_gpc()){
$_GET =array_m ap('stripslashes', $_GET);
$_POST = array_map('stripslashes', $_POST);
$_COOKIE = array_map('stripslashes', $_COOKIE);
}
As a PHP developer and PHP programmer, you have lots of responsibilities while developing and securing PHP web applications, and guess what? we know all your pain.
This article is here to help you out figuring out all the faults and flaws and to give you all the best and possible solutions to get you out of the situations. You can become a good PHP programmer by having good PHP training.
The best and the most important thing is to understand how you can secure your website and to know all the tools and software to use.
If you liked this article give it a like and follow us. If you have any question or any issue and you want to become a PHP champ , just comment us below.
Design
Art
AI
Development
Apps