PHP is the most popular programming language and is being widely used for rapid development of dynamic websites. Web servers are publically accessible, so they possess possible security vulnerabilities.
PHP is a stable and almost an inexpensive web application platform. Like other web-based platforms, PHP is unsafe from external attacks too. For this, developers, database architects, and system administrators should take measurable precautions before deploying any PHP applications to a live server. These security techniques can get done with a few lines of code or some little adjustment to your application settings.
In this blog here, I have described in detail some of the most common vulnerability found in PHP web applications along with suggestions as for how they can be managed and prevented.
SQL injection is the most common hacking type and specifically targets the database-driven websites or web applications which link or interacts with databases. The SQL injection is a type of code injection, where attackers make full use of the vulnerabilities in the website security measures to send special SQL queries to the database which can modify it and tables within it or delete the whole database.
Get free quote from professional PHP Development Company about your project.
This type of attack occurs when the developers fail to check data validation functionality in those areas of the website where the data from external sources can be inserted into the website. The attacker can easily add their own SQL statements in unprotected SQL queries which utilize data submitted by the user to check for something in the database.
An unprotected statement would be something like this
| 1 | $query = “SELECT * FROM users WHERE username = ‘niki’”; |
An SQL injection query will result in the following attempt:
| 1 | $query = “SELECT * FROM users WHERE username = ” or ’1=1′”; |
The result generated here will be true, and thus the content of entire table users would be displayed.
[related_posts]
In the SQL injection, attackers gains access to all the information in the database such as passwords, usernames, emails, and some other sensitive information.
Remote File Inclusion and Remote Code Execution
The violation of this security measure will allow malicious or even unknown third party to run any code on the web server or on the client side and can even lead to other hacking attempts.
Remote file inclusion caused by a website susceptibility which lets the hackers to deploy malicious file on the web server. This can happen because of improper use of require() and include() functions if the register_globals directive, is ON, allowing the user to initialize variables remotely. These remote variables can be used to include malicious or unwanted files from remote locations, and if the allow_url_fopen is enabled in php.ini, then remote files can also be uploaded to the site’s server via FTP or HTTP from any remote location.
Cross Site Scripting is one of the most common forms of hacking Hackers use a legitimate site’s vulnerability to forcefully makes the site to do certain things. In XSS, the hacker infects a web page with the malicious client-side script and whenever a user visits that page, the script gets downloaded into the attacker’s browser and executed. The pattern of XSS attack is depicted in the diagram below:
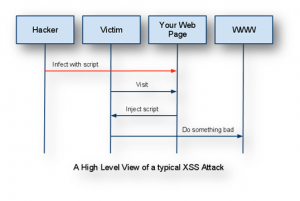
The session and cookie hacking can’t violate the database or the web application itself, but it can affect user accounts. A session is an entity triggered when users establishes contact with any web server and consists of some period of interaction between users and web application which may be authenticated using security measures like a username and password. In all this session, the web application stores a cookie or file on the user’s’ browser, which contains information about the session such as users’ preferences, authentication data, unique codes or shopping cart information and more.
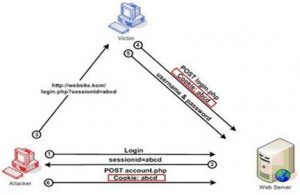
Directory aka Path traversal is a method of destroying web applications by accessing the files from the document root directory which allows attackers to view restricted files and interact with the web server by executing commands. This hacking attacks happens from the browser and get done by entering URL into the address bar which helps to let out of the root directory and into the main server directories. This attack can also be done through input portals on the front end of the web application.
Security is an important phase in all the process. In this blog, I have mentioned here the top five PHP security measures to follow. Still got questions or need more information? Do comment below.