Latest Blogs
Business Process Outsourcing
Ramsha Khan
May 22, 2025
Implementing a Robust Revenue Cycle Management System
Read More...

Implementing a Robust Revenue Cycle Management System
When you’re running a healthcare facility, whether it’s a clinic in France, a hospital in Germany, or a private practice in the UK, managing the financial side of things can get really complicated. That’s where Revenue Cycle Management (RCM) comes in. And if you’re wondering things like What is revenue cycle management and why is it important?, you’re in the right place.
The RCM market is said to go above $238 billion by the year 2030. So, let’s break down exactly what RCM is, why it matters, and how you (yes, you!) can implement a robust and effective RCM system in your healthcare practice. Think of this as your no-nonsense, step-by-step guide tailored especially for healthcare providers across Europe.
Let’s start with the basics. Revenue Cycle Management in healthcare refers to the financial process that healthcare facilities use to track patient care episodes from registration and appointment scheduling to the final payment of a balance.
In simpler terms, it’s everything that happens between a patient walking through your doors and you getting paid for treating them.
So, what is revenue cycle management in medical billing? It’s the engine behind ensuring claims are submitted properly, payments are collected, and nothing falls through the cracks.
You could be offering the best patient care in the region, but without an efficient revenue cycle, your practice may struggle financially.
Here’s what is the purpose of revenue cycle management:
And for hospitals, the stakes are even higher. What is hospital revenue cycle management? It’s the backbone of financial operations, helping large systems manage complex workflows, insurance contracts, and high patient volumes.
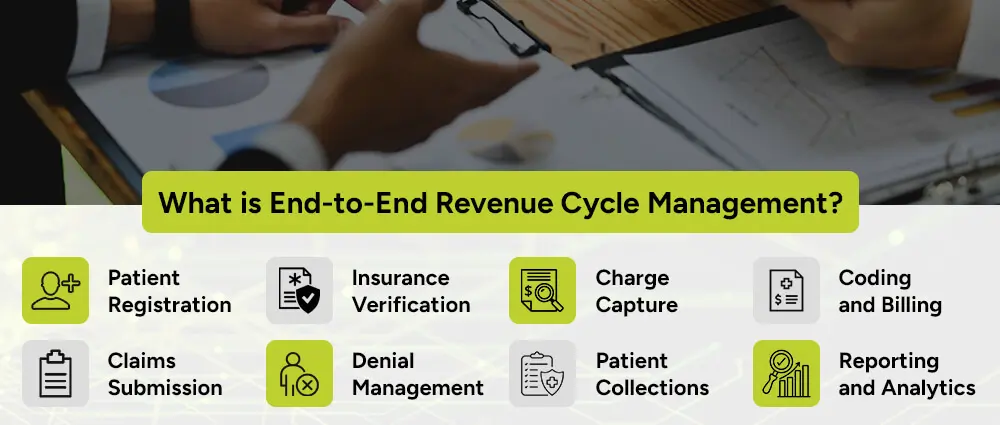
End-to-end RCM covers the entire process, starting from the moment a patient schedules an appointment to the point when the bill is paid in full.
This includes:
This is the first and foundational step of the revenue cycle. During registration, patient information such as demographics, contact details, and insurance coverage is collected and recorded. Accurate registration is crucial as any error here can affect the entire billing process.
European healthcare providers must often verify insurance through government-funded programs or private insurers. This step ensures patients are entitled to specific treatments under state-funded coverage or private health plans. Verifying eligibility and co-payment responsibilities helps prevent billing surprises and improves the patient experience.
Charge capture is the process of documenting the services provided to a patient during a visit. Whether operating under Diagnosis-Related Groups (DRG) systems or private billing models, charge capture is essential.
This process records the clinical services provided and converts them into billable items. Inaccurate or incomplete charge capture can lead to underbilling and lost revenue, especially in countries transitioning to value-based care models.
Medical coding involves converting diagnoses, procedures, and medical services into standardized codes. European healthcare billing must comply with international coding standards such as ICD-10 and CPT/HCPCS, as well as country-specific requirements. This is just like how the US healthcare providers are expected to follow the HIPAA-compliant cloud storage for healthcare Professionals.
Proper coding ensures accurate billing, whether dealing with national health services or private insurers. It also supports compliance with cross-border care regulations under the EU directive on patients’ rights
Once the billing is completed, claims are submitted. Delivering claims efficiently, whether to national health authorities, insurances, or third-party payers, is key to timely reimbursement. European healthcare providers often deal with a mix of funding sources, so it’s critical to tailor submissions to meet the criteria of each payer.
Denial management involves identifying, analyzing, and correcting claim denials to ensure payment is received. Managing and reducing claim denials is especially important in Europe, where billing systems can vary greatly between countries and even regions.
A strong denial management system helps providers understand the reasons behind rejections, correct issues quickly, and secure reimbursement. This ensures that providers can maintain healthy revenue streams and meet financial targets.
Once insurance payments settle the bill, the responsibility for any remaining balance lies with the patient. In Europe and especially in countries with a private insurance or co-payment system, it has become more common for organizations to pursue the collection of balances from patients. Further enhancements in collection rate are seen with transparent billing systems, multilingual invoices, and flexible payment plans that build patient trust and satisfaction.
With reporting and analytics, insights into the financial health of the revenue cycle management process and operational performance are derived. Continuous analysis is, therefore, required for identifying bottlenecks, tracking KPIs, and improving the processes.
Some reporting and analytics aid in European healthcare chooses to monitor key areas like Days Sales Outstanding (DSO), denial rates, and payment turnaround.
This is what makes up the revenue cycle management process and why it’s so essential to get it right.
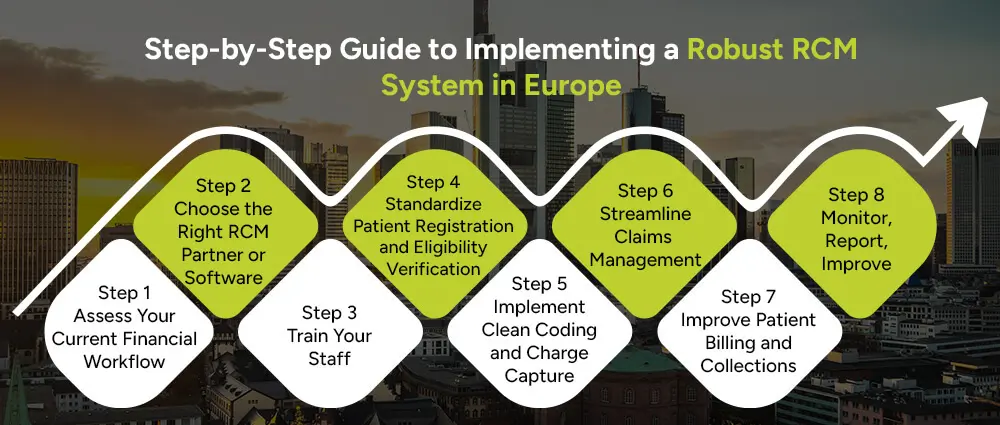
Here’s your roadmap to building a solid revenue cycle management system from the ground up:
Take a hard look at your existing billing process. Are claims often rejected? Are you struggling with collections? Identifying the gaps is the first step.
Whether you hire a third-party revenue cycle management services provider or invest in an in-house system, make sure the solution:
Everyone, from admin, billing team, and clinicians, all should understand the RCM process. Training ensures fewer data entry errors and smoother claims handling.
Incorrect patient data is one of the biggest reasons for claim denial. Set clear protocols for collecting accurate info and verifying insurance coverage upfront for the Paitient portal.
Work with trained medical coders who understand both ICD-10 and local European healthcare coding systems. Consider automation to reduce manual entry errors.
Automate claims submissions and track denials in real time. A good RCM system can flag errors before they even get sent to insurers.
Make it easy for patients to understand their bills. Offer digital statements, multiple payment options, and set up automated reminders.
Use data analytics to review how your revenue cycle is performing. Identify trends like frequent claim denials or delayed payments and fix them proactively.
While the revenue cycle management for hospitals in the U.S. often deals with private insurers and CMS regulations, Europe is more nuanced with its mix of public and private systems. Still, the principles of end-to-end RCM apply on both sides of the Atlantic.
European providers should ensure their RCM solutions are:
With rising operational costs and tighter margins, efficient revenue cycle management is no longer a luxury, it’s a necessity. Implementing a smart revenue cycle management system with good Medical Practice IT support, like Arpatech, can help you stay financially healthy while focusing on what truly matters: patient care.
Let’s make you efficient and successful!
Revenue lifecycle management is the broader process of managing all revenue-related activities, from service delivery to payment collection, including forecasting and reporting. It often overlaps with RCM but is a more holistic, business-oriented term.
The three main components of revenue cycle management are:
The three pillars of RCM are:
Ramsha Khan
May 22, 2025

How Much Does Epic Cost in 2025 in Europe
If you’ve ever wondered how much does Epic cost in 2025, especially in Europe, you’re not alone. Whether you’re a healthcare provider, a hospital administrator, or just someone curious about healthcare tech, Epic has probably popped up on your radar.
But before we dive into the cost side of things, let’s take a step back, what exactly is Epic, and why is it such a big deal?
Epic Systems is one of the biggest names when it comes to healthcare software. They offer electronic health records (EHRs), medical billing tools, patient engagement apps, basically everything a healthcare provider might need to keep patient information organized and secure.
Whether you hear people asking how much does Epic EMR cost, or how much does Epic medical software cost, they’re all talking about this same ecosystem of tools that power some of the world’s best hospitals and clinics.
Epic is widely praised for how smoothly it connects different parts of the patient experience. From the moment you walk into a clinic to the follow-up email you get after a surgery, Epic can power it all behind the scenes. Pretty cool, right?
In my opinion, one of Epic’s biggest strengths is how scalable it is. A large hospital group and a small private practice can both find value in using it (though the setup would obviously look a little different).
It is also equipped with features such as telehealth, patient portals, advanced analytics, and even AI recommendations for doctors. A lot of people are curious: How much does Epic cost for a hospital? How much are Epic EHR monthly fees? Such is the capacity of the software that many feel it should be worth the investment.
Now, let’s talk a little bit about the cost side, without drowning in too many numbers.
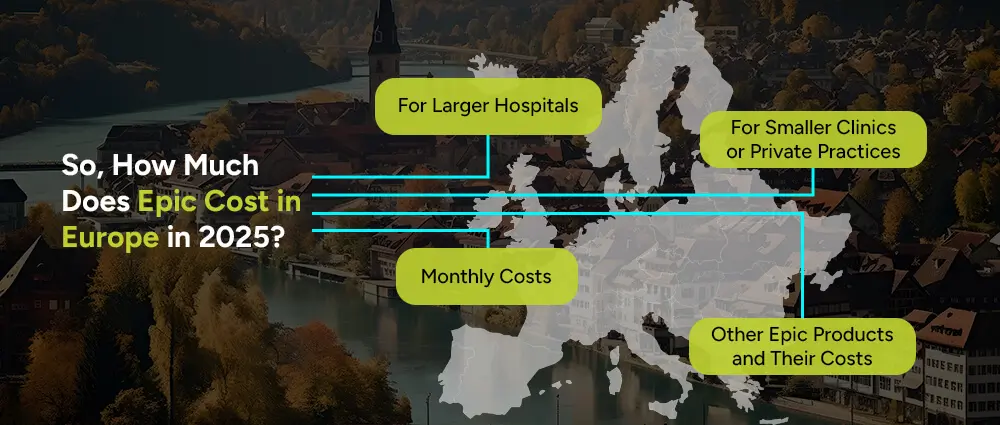
First, it’s important to know that Epic doesn’t really have a one-size-fits-all price. It depends on factors like the size of your practice, the number of users, and how complex your needs are. That’s why you’ll often hear questions like how much does Epic cost for a clinic versus how much does Epic cost hospital, because they can be very different!
In Europe in 2025, Epic pricing still follows the general trend of being a premium option.
You’re typically looking at a multi-million euro investment, but again, this covers the software, licensing, and often a lot of training and support too. You are also obligated to follow certain protocol and be HIPAA compliant cloud storage for healthcare Professionals.
You’ll still find that Epic is one of the more expensive options. People searching how much does Epic cost for a small clinic or how much does Epic cost for a private practice will find that costs can be relatively high compared to more lightweight solutions.
If you’re wondering how much does Epic EHR cost per month, it usually isn’t billed monthly the way some subscription services are. Most agreements are long-term, often structured around yearly licensing and support.
In short: Epic tends to be a significant but long-term investment, particularly favored by institutions that want a comprehensive, reliable system.
You might have heard about other Epic products like Epic Universe, their next-gen platform integrating even more patient services, AI, and mobile support. So if you’re asking how much does Epic Universe cost, just know it’s currently bundled into broader service agreements and remains a premium offering in 2025.
Several factors affect how much Epic software costs:
Implementation support: Epic often requires dedicated consultants for setup, training, and optimization.
Ongoing support and maintenance: Regular updates and helpdesk services are usually part of a service contract.
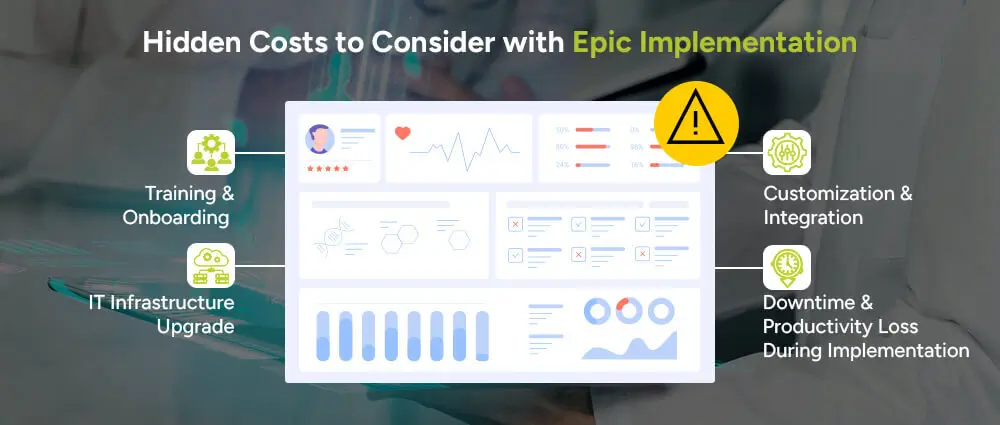
When evaluating Epic for your healthcare organization, it’s crucial to recognize that the initial sticker price is just the beginning. There are several hidden costs that can significantly impact your budget and planning. Here are some important “gotchas” to keep in mind:
Training properly is vital to the success of an Epic rollout, but it can prove extravagant. In my opinion, organizations often underestimate this cost. Training and onboarding costs can easily be beyond €100,000 depending on the size of the staff, while big hospitals or healthcare systems can spend much, much more. This includes initial and ongoing training, costs for trainers, development of custom training materials, certification programs for key users, and need for refresher courses as time passes and the system changes.
Epic’s software is quite heavy in its performance and resource usage. Your current infrastructure such as IT, servers, storage, cloud, healthcare IT Support Services, and network bandwidth may require a huge makeover to meet Epic’s performance and security requirements. In my opinion, this can be a hidden iceberg: hardware, cloud service, cybersecurity solutions, and IT staff expansion costs wind up tacking on hundreds of thousands more to the total cost of the project.
It is flexible, yet costly to make hidden costs known in the integration of other existing laboratory systems, imaging equipment, Patient portal software, billing systems, insurance portals, and outside applications. Usually, this involves engaging a consultant with specialized knowledge, middleware solution, and extensive testing, thus greatly increasing the total cost of the project. Without careful budgeting for the taking up of costs due to integration, it may become a much greater cause for delay and budget overruns than you have ever seen.
There will be a learning curve no matter how much you prepare for the change to Epic. Your staff will be productively spending time with new workflows and away from patient appointments and, therefore, it will reduce productivity in the short term. Some partial downtime may occur on the system while migrations or updates are in effect, thus further temporarily disrupting operations. Even in my view, therefore, one must plan for a period of reduced operational efficiency, stretching at least to several months, and assign additional resources to help bridge the gap.
Honestly? It depends on what you need. Epic is like the Mercedes-Benz of EHR systems. It’s sleek, powerful, and made for serious healthcare players. But if you’re a small practice just starting out, it might be like buying a Ferrari to drive to the grocery store.
That’s why when you hear people ask things like how much does Epic cost per year or how much does Epic Systems cost, it’s so variable. It’s almost like asking, “how much does a car cost?”, it depends on the model, the features, and the size.
In the end, when asking how much does Epic cost, it’s really about asking how much you’re willing to invest in a long-term healthcare solution and medical practice IT support. It’s not cheap, but it’s designed to be powerful, secure, and future-proof. So, get the expertise of software developers and IT support staff at Arpatech to get the best software update for your healthcare system.
Implementation costs for Epic in a hospital can easily reach into the millions of euros. It includes licensing, infrastructure, training, customization, and support. Big hospitals often see this as a necessary long-term investment to provide top-tier patient care.
For general EMR systems (not just Epic), costs can range widely, from a few thousand euros a year for basic setups, to millions for enterprise-grade solutions like Epic. Cloud-based EMRs tend to be more affordable upfront compared to on-premise giants.
Ramsha Khan
May 20, 2025

Patient Portal Software Development Guide: Types, Featu...
Healthcare has gone digital. Today’s patients want convenience, and healthcare providers want streamlined processes. That’s where patient portal software comes in.
Whether you’re a hospital admin or a health-tech startup founder, this guide breaks down everything you need to know about patient portal software development in 2025: from types and features to cost and compliance.
Patient portals: secure online accommodations for patients to access their medical records, communicate with providers, and manage their care at their convenience at any time of the night or day. These offer personalized and yet transparent healthcare experiences that can find an apt place in between patients and their healthcare providers.
Think of it like online banking, but for your health.
Thus, healthcare is moving at quite a pace, and patients expect more in controlling their health journeys. Patient portal software development thus helps them realize the above-mentioned goals through reduced paperwork, increased transparency, and the establishment of less time-consuming channels of communication.
It also enhances compliance, thus increasing patient satisfaction, which are the two primary objectives in modern healthcare.
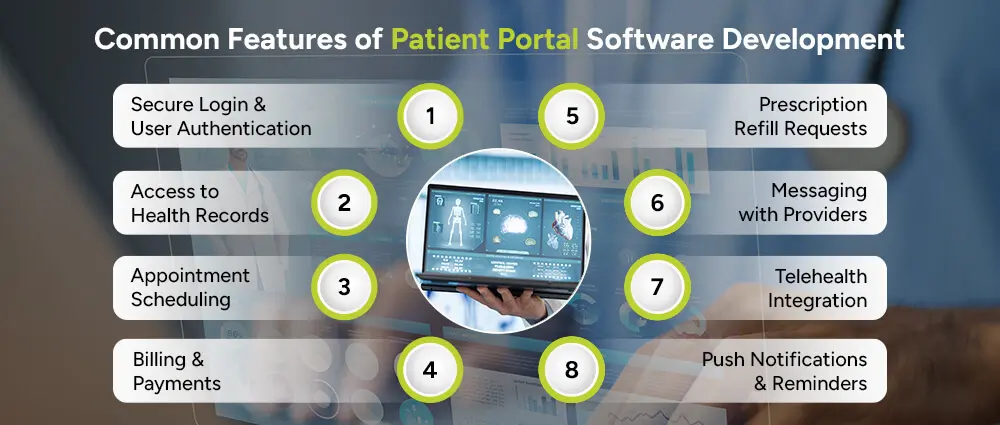
When you’re planning patient portal development for healthcare providers, these features are typically essential:
Patients must log in through a secure portal, often using two-factor authentication to ensure data is protected against unauthorized access.
Health access would allow patients to view their lab results, diagnoses, prescriptions, and past visit notes, putting them in charge of their health.
The patient can use the portal to book or reschedule appointments or cancel them without having to call up the clinic or wait in line.
Securely view medical bills, make payments online, and access insurance coverage information, all in one place.
Rather than calling a clinic, patients can request medication refills through the portal with just a few clicks.
Patients can send secure messages to their doctors, nurses, or administrative staff for non-emergency concerns and follow-ups.
The integration of telehealth services in the portal includes video consultations, which provide patients with easy access to care from home.
Patients receive automatic alerts reminding them of upcoming appointments, test results, and unread messages, thus keeping them in the know.
As patient expectations grow, modern patient portal app solutions are becoming more intelligent and personalized:
Integrated AI tools help patients identify possible conditions and guide them toward the right care without immediate doctor input.
Based on medical history and lifestyle data, the portal can deliver tailored health recommendations and reminders.
Sync with devices like smartwatches to track vitals such as heart rate, steps, or blood pressure in real-time.
Portals now offer interfaces in multiple languages to improve accessibility for diverse patient populations.
Features like screen readers, text enlargement, and voice navigation support patients with visual or physical disabilities.
Authorized caregivers or family members can manage medications, view test results, and book appointments for their loved ones.
The value of patient portal software lies in the variety of data it can handle, all from a single platform:
Patients can view their medical history, diagnoses, test results, and immunization records at any time.
Especially important for children, travel, and public health events, this data helps patients stay current on required vaccines.
Patients get notified and can review lab results as soon as they’re uploaded, often faster than waiting for a call.
After each appointment, patients receive a summary including physician notes, treatment plans, and prescribed medications.
Personalized care plans are accessible online, helping patients stay on track with medications, therapy, or follow-ups.
Complete lists of prescribed drugs with refill tracking help avoid medication errors and improve adherence.
Patients can check what their insurance covers, view balances, download invoices, and pay bills online.
Physicians can upload progress updates, allowing patients to track their recovery and understand next steps.
Depending on the healthcare setting, user requirements, and cloud software, different types of patient portal software can be developed:
These are developed as independent solutions and are often preferred by small practices that don’t have existing EHR systems.
These are connected to the provider’s existing Electronic Health Record system, creating a seamless data exchange between doctors and patients. This way, the providers can effortlessly provide healthcare IT support services in Dubai to doctors or patients if they find any glitch in the IT matrix.
Designed for smartphones and tablets, these apps give patients access on the go, perfect for busy individuals who need health data at their fingertips.
Built from the ground up, these are customized to the exact needs of a clinic, hospital, or health network, offering maximum flexibility and branding.

You’re probably wondering: how much does it cost to develop a patient portal? Here’s what to expect based on complexity:
Costs include design, development, testing, deployment, healthcare cloud migration, and post-launch support. A skilled custom patient portal development team can guide you in optimizing budget and features.
In 2025, patient portal software development is not just about digitizing medical records, it’s about empowering patients, improving outcomes, and making care more accessible for every person.
Whether you want to create a basic solution or a feature-rich platform, investing in a patient portal helps future-proof your healthcare delivery model. At Arpatech, our software development services are top-notch. Partner with our expert software and cloud experts and get future-ready patient portal today.
Typically, a basic version may take 3–4 months to put together. Highly customized and feature-rich portals may take 6–9 months or more to make, especially in cases wherein complex integrations and compliance testing are involved.
Portals apply a variety of cybersecurity applied by encryption, secure login protocols, audit trails, and role-based access control. They are also subjected to regulation, such as HIPAA-compliant cloud storage for healthcare professionals in the USA, ensuring the security and confidentiality of patients’ information.
Key features in a patient portal software include:
Advanced features might include telehealth, AI chat, and wearable integrations.
If you’re thinking about developing your own patient portal software, now’s the time to act. Let’s talk about how to bring your vision to life.
Ramsha Khan
May 15, 2025

Medical Practice IT Support in the USA: What You Need t...
Let’s be honest, running a medical practice is no small feat. From managing patient records to ensuring HIPAA compliance, there’s a lot going on behind the scenes. And guess what keeps it all running smoothly? Yup, you guessed it, IT support for medical practices.
Whether you’re a small clinic or a multi-location medical office, having reliable IT services for medical practices isn’t just helpful, it’s essential. So, if you’re wondering what medical practice IT support really means and why it’s such a game-changer, keep reading. We’re breaking it down in simple terms!
It’s like having a behind-the-scenes tech team of all your medical ventures – that’s what medical practice IT support is all about. Cunningly packed, they keep all your computers and software, patient management systems, and data security always running like a well-oiled machine.
From network establishment to troubleshooting slow systems of the calamity hour, the IT support for the healthcare sector ensures that an employee may concentrate on doing the best they can: patient care.
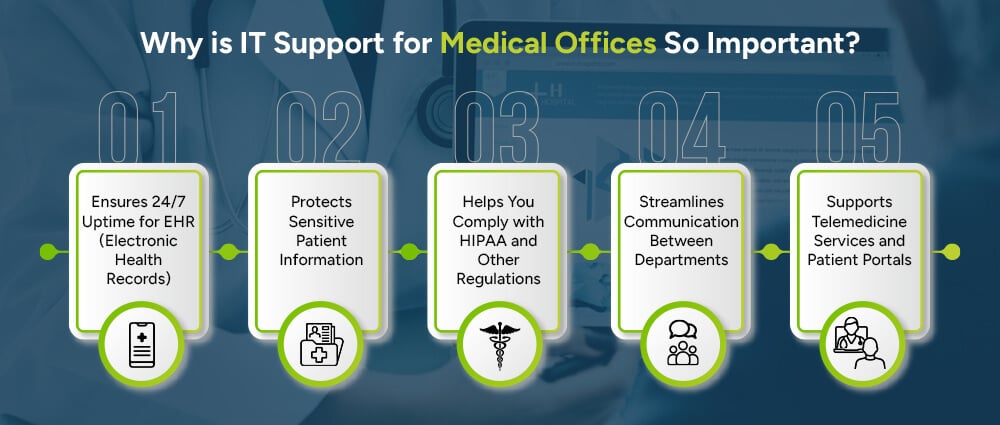
Ever tried to check a patient’s chart and the system crashes? Or worse, faced a cyberattack that puts confidential data at risk? That’s where medical office IT support steps in to save the day.
Some real-life reasons why IT support for medical practice services are a must:
EHR systems are the lifeblood of any current medical practice. If they go down, even for a few minutes, the entire workflow can come to a halt. Reliable IT support ensures that your records are available when needed, keeping patient care in progress and stress levels low.
Patient data are highly confidential, and hackers know that. With professional IT support for the healthcare sector, your systems are equipped with the best security tools such as encryption, firewalls, and secure login protocols to keep all information secure
HIPAA compliance isn’t optional, it’s the law and its necessary. And the rules are pretty strict when it comes to protecting patient data. A trusted IT support provider ensures your systems meet all legal requirements, helping you avoid penalties and stay compliant at all times.
When your systems are connected and running smoothly, communication becomes a breeze. From front-desk check-ins to back-office billing, IT support medical practice solutions help everyone stay in sync without delays or tech hiccups.
With more patients relying on virtual care and online access to their records, your tech needs to be on point. IT support helps set up and maintain secure telehealth platforms and user-friendly patient portals so everyone stays connected.
Great question! Not all IT support is created equal, especially when it comes to IT support for medical clinics. A solid service provider will offer the following essentials:
When tech issues pop up, which they do unannounced all the time, you need help right away. A 24/7 helpdesk gives your staff access to IT pros anytime, whether it’s a slow computer or a login issue before a busy morning shift.
Accidents, power failures, or ransomware attacks can wipe out important files in seconds. That’s why regular backups and a strong recovery plan are must-haves. Your IT team makes sure data is backed up and easy to restore if something goes wrong.
IT support doesn’t just fix things, it prevents problems too. With constant monitoring, your network can alert technicians of any weird activity or performance drops before they become a major headache.
IT pros who specialize in medical offices know the ins and outs of HIPAA. With HIPAA-compliant cloud storage for healthcare professionals can make sure their systems are updated, secure, and follow all the rules to keep them in compliance and out of legal trouble.
Electronic health record (EHR) systems and electronic medical record (EMR) systems are highly complicated to implement. The IT personnel in your organization will need to make sure that more or less everything is kept in order during the installation and that any updating is overseen as expediently as possible in order to minimize disruption to the system environment.
Cyber threats are real and growing. From phishing scams to malware, there are multiple forms of cyber threats out there. Cybersecurity is on the rise and getting closer to reality every day. IT experts set up antivirus tools, firewalls, and encryption to ensure that patient data is secure.
Whether you need more storage or flexible work options, cloud services are a game-changer. Your IT support provider can help you move safely to the cloud and set up secure, HIPAA-compliant access for your staff.
So, if you’re looking for reliable medical practice IT support solutions, make sure your provider covers all the bases above.

Here’s how professional IT services for medical practices can seriously level up your operations:
When systems run fast and smoothly, your patients spend less time waiting and more time receiving care. Everything from check-in to prescriptions becomes quicker and more efficient—boosting satisfaction across the board.
Unplanned system outages can cause chaos. Reliable IT support means your software and hardware are monitored and maintained regularly, drastically reducing the chance of downtime during critical hours.
Cybersecurity threats can be devastating for medical offices. A good IT team defends your systems with firewalls, antivirus programs, and regular updates. Cybersecurity solutions for healthcare sector protect both your patients’ data and your clinic’s reputation.
IT issues can cost you time and money, especially if they result in system failure or data loss. With proactive support, many issues are fixed before they escalate, saving you from big repair bills or legal fines.
Instead of your team scrambling to fix a printer or troubleshoot a login error, they can concentrate on providing great care. IT support takes care of the tech stuff so your staff can do what they do best.
Technology is the backbone of modern healthcare cloud migration, and your practice deserves IT support that’s just as reliable as your care. Whether you’re starting fresh or looking to upgrade your current setup, choosing the right IT support for medical offices can help your practice run smarter, safer, and smoother.
Need help finding the right IT support for your medical practice? Look for companies working worldwide. From healthcare IT support services in Dubai to the USA, Arpatech is offering solutions internationally.
Let’s connect with the best IT Support Service Professionals today!
Outsourcing means you get expert-level support without having to hire an in-house team. That’s a big win in terms of cost, skill level, and round-the-clock coverage. You’ll also stay ahead of the tech curve without having to research every new update or regulation.
Costs can vary based on the size of your practice and the services you need. On average:
Some providers offer flat-rate plans, while others charge per device or per user. It’s always a good idea to get a custom quote based on your specific setup.
Ramsha Khan
May 13, 2025

Healthcare IT support services in Dubai – UAE
Working in healthcare instead of medical issues, are technical issues giving you a headache?
Well, you’re not alone.
It’s a high-tech, data-driven world, and behind every smooth-running hospital or medical center is a powerful IT system that makes it all possible. If you want your clinical business or hospital to survive in today’s landscape, with protected patient care and patient info, you must get robust IT infrastructures installed in your systems.
Healthcare today isn’t just about doctors, nurses, and clinics anymore. If you’re in Dubai or anywhere in the UAE, you’ve probably noticed how fast the healthcare sector is growing. But here’s the catch: managing the tech side of things isn’t easy. That’s where Healthcare IT Support Services come into play.
Whether you’re running a clinic, a large hospital, or even a specialized lab, having the right IT support is no longer optional, it’s essential.
The healthcare industry has unique requirements. Unlike other businesses, there’s no room for error. Patient records need to be secure, systems should be fast and reliable at all costs, and downtime? That’s simply not acceptable.
That’s why IT support services in healthcare have to be more than just tech troubleshooting. They need to be strategic, responsive, have a strong incident management system, and, most importantly, be healthcare-focused.
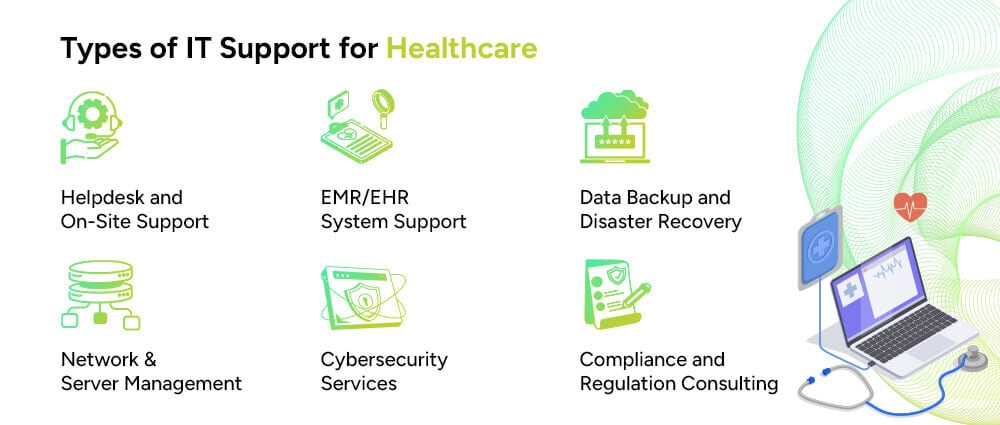
Not all IT support is the same. Here’s a quick breakdown of the main types of IT support services for healthcare companies:
Round-the-clock support for fixing everyday issues, from login problems to broken printers in medical offices. With IT resource allocation services, tech teams ensure that all problems are solved by dividing resources effectively.
Electronic Medical Records and Electronic Health Records need expert handling. Healthcare IT teams ensure that they provide top-tier user access management and that they’re secure, accessible, and working without any glitches.
What happens if your system crashes? With healthcare-managed IT support services, your data is regularly backed up and can be restored in no time.
Hospitals need reliable network systems. With the right DevSecOps service teams and IT teams monitoring traffic, preventing outages, and optimizing performance, you’ll get the best networks and server management.
Healthcare data is a top target for hackers. IT support services implement firewalls, encryption, access controls, and 24/7 monitoring to protect sensitive patient information.
Healthcare providers in the UAE must comply with local laws like DHA and international standards like HIPAA. That’s where healthcare IT support services consulting becomes vital.
Think of the healthcare IT system like a human body with many parts working together to stay healthy. Here are some vital components:
EHR systems are electronic means of storage where patients’ medical history, diagnosis, medication, treatment plan, and laboratory results are kept digitally. It provides accurate real-time information for easier and better clinical decisions shared by the health provider.
PACS allows medical images like X-rays, CT scans, and MRIs that may be stored, retrieved, and sent electronically. It does away with the physical films, thus speeding up the process of diagnostics and enabling distance consultations.
This software handles the administrative side of healthcare, appointment scheduling, billing, claims processing, and patient registration. It streamlines workflow and helps clinics operate more efficiently.
Telemedicine enables virtual consultations between doctors and patients through secure video conferencing tools. It expands access to care, especially in remote areas, and supports follow-ups and chronic condition management.
HIE systems facilitate safe health information transferring among various health care organizations. That way, continuity of care may be achieved, especially when patients are shifted from one provider to another, from one hospital to another, or from one clinic to another.
Cybersecurity technologies, used by healthcare facilities to safeguard sensitive data from breaches, ransomware, and threats, include firewalls, encryption, multi-factor authentication, and real-time threat monitoring.
Mobile apps help patients track fitness, medications, appointments, and chronic conditions. On the provider side, apps can assist with accessing EHRs or telemedicine services on the go, boosting convenience and engagement.
With the help of IoT devices, like smart heart monitors, glucose meters, and wearable fitness trackers, you can collect real-time patient data. This enables proactive care, remote monitoring, and better chronic disease management.
All of these need specialized, healthcare-specific IT support services to function smoothly and securely.
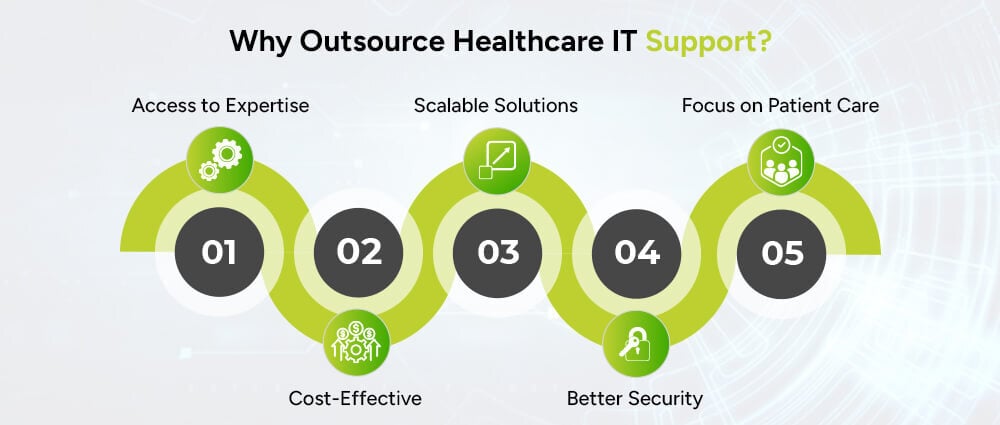
You might be thinking; shouldn’t we just hire our own team?
Great question. But here’s why outsourcing healthcare-managed IT support services might actually be a better move:
You get a team with experience in healthcare IT services and support, not just generic tech support. They utilize the comprehensive IT help desk supporting ticketing system to organize all incidents and issues and effectively prioritize each problem.
Hiring, training, and managing an in-house team is expensive. Outsourcing saves time and money.
Whether you’re expanding or integrating new technology, outsourced teams can scale with you. This way, ultimately, you can go from a small clinic to a large hospital with loyal patients and robust overall IT connections.
Reputable IT support companies offer top-tier cybersecurity, data encryption, and compliance strategies.
Let IT pros handle the backend while your medical staff focuses on what they do best—caring for patients.
There are several healthcare IT companies in the UAE, but look for those that offer:
In today’s digital healthcare landscape, having the right IT support services for healthcare isn’t just a luxury, it’s mission-critical. Especially in a tech-forward city like Dubai, where innovation meets high expectations, healthcare providers must keep up with the pace.
Whether you’re a small clinic or a large hospital network, investing in the right healthcare IT help desk support services can help you run more efficiently, protect patient data, and focus on what matters most, delivering quality care. We, at Arpatech, believe that with optimal IT infrastructure, you can deliver the best healthcare possible.
So, let’s connect today!
IT in healthcare plays a vital role in managing patient data, supporting clinical decisions, enabling telemedicine, ensuring compliance, and improving operational efficiency. It’s the backbone that supports better, faster, and safer patient care.
There are several top-tier IT providers in Dubai and the wider UAE that specialize in healthcare. Some popular names include Injazat, MENAITech, and bespoke local providers offering healthcare-specific IT support services. Always evaluate based on your facility’s size, needs, and budget.
It’s a valid concern, but only if you’re working with the wrong provider. Trusted IT support companies use advanced cybersecurity protocols, encryption, and round-the-clock monitoring to improve your data security, not weaken it. Just make sure they have experience with healthcare managed IT services support and meet UAE compliance standards.
Ramsha Khan
May 8, 2025

HIPAA-Compliant Cloud Storage for Healthcare Profession...
For healthcare professionals in the U.S., HIPAA dictates what can be used, and they essentially should be taking one priority above all else: compliance with the rules. Under the Health Insurance Portability and Accountability Act HIPAA, the standard has become that sensitive patient information will be held as proprietary as more and more providers become cloud-centric and reliant on technology-based solutions for documentation and communication, and thus, ensuring HIPAA-compliant cloud storage is paramount.
Today’s focus will be on why specific cloud storage is HIPAA compliant, the importance of it in the healthcare field, and how exactly one should choose the best HIPAA-compliant cloud storage solutions for their practice. Whether big or small, every system has to know and implement the cloud format for storing data that ought to be HIPAA compliant in its operations to keep patients’ trust safe and satisfy all legal requirements.
It is essential in modern healthcare to have fast yet safe and dependable patient information access. Electronic health records (EHRs) and everything they hold lab results, imaging files, etc. The data run high, and so do the responsibilities surrounding its safety.
Cloud storage HIPAA-compliant solutions allow healthcare professionals to:
Patients’ histories, medications, and notes can be accessed anytime, anywhere by clinicians through HIPAA-compliant cloud-based storage, allowing mobile devices and flexible, responsive care.
Easier data-sharing between departments or practices may lessen miscommunication and delays in treatment plans, as well as allow greater coordination of care across the establishment.
There are facilities in-built for disaster recovery in the HIPAA-compliant cloud storage software protecting against all forms of hardware failure, cyberattacks, or natural disasters.
By migrating to the cloud architecture and using compliant storage, providers can ensure that patients receive timely, well-informed care while keeping sensitive data protected from breaches.
However, not all cloud storage is created equal. So, is cloud storage HIPAA-compliant by default? Not necessarily.

To be considered HIPAA-compliant cloud storage, the role of cloud-managed services is to implement several technical, physical, and administrative safeguards. These include:
Both at rest and in transit, encryption and cloud cryptography ensure that even if data is intercepted or accessed without authorization, it remains unreadable to malicious actors.
This means role-based access and multi-factor authentication. This way only authorized individuals would have access to patient data, and access must be limited based on job roles to minimize risk.
Logging and monitoring user activity enables you to have audit logs that help you track who accessed what data and when it was accessed. This helps support transparency and detect suspicious activity.
This feature enables authorities to prevent unauthorized access. Inactivity triggers an automatic logoff, protecting against situations where a user forgets to sign out from a shared or public device. So, whether you use a private or hybrid cloud, your user data is safe at all ends.
The provider must sign a BAA outlining their responsibilities. A BAA is a legal document that ensures the cloud provider is contractually bound to safeguard PHI (Protected Health Information).
Without these features, cloud storage is not considered HIPAA compliant.
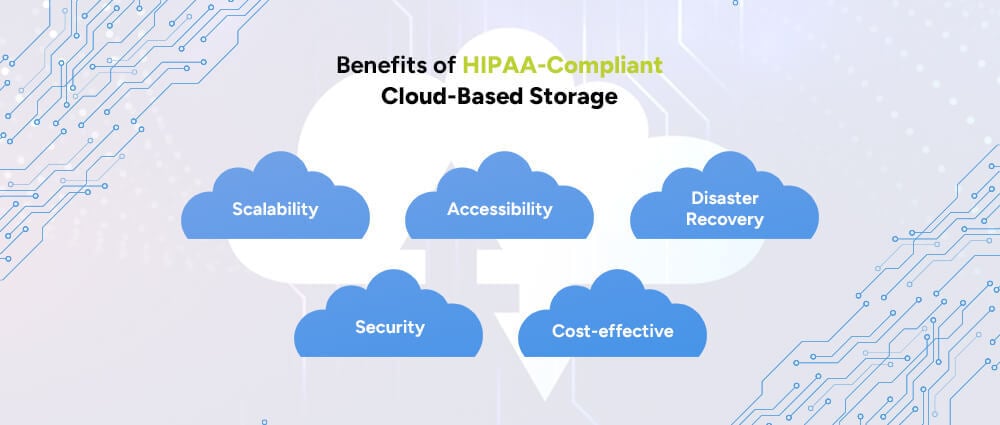
Choosing HIPAA-compliant cloud storage software offers many advantages:
If you have started small in a clinic, easily grow with your practice. Whether you’re a solo practitioner or expanding to multiple clinics, HIPAA-compliant cloud storage solutions can adapt to your data needs without major infrastructure changes.
Pay for what you need, when you need it. Instead of investing in expensive on-site servers, cloud Cost-optimization of HIPAA-Compliant Cloud-Based Storage enables you to only pay for the cloud resources you use, which helps manage budgets better.
Access records securely from any device or location. Clinicians can review files from home, during emergencies, or on the go, improving continuity of care and patient outcomes.
Take advantage of Advanced encryption and access protocols to keep data safe. Cloud based storage HIPAA compliant systems employ strong security standards to reduce the risk of unauthorized access or data leaks.
Backups ensure that data isn’t lost in emergencies. HIPAA compliant cloud storage solutions regularly back up data and have plans in place for quick recovery, so healthcare services aren’t disrupted during crises.
This not only improves operational efficiency but also strengthens patient care in a HIPAA-compliant cloud by making vital information available when and where it’s needed most.
If you’re wondering what cloud storage is HIPAA-compliant, here’s a list of some of the best HIPAA-compliant that effectively work with cloud infrastructure management in the USA:
Small healthcare practices often assume HIPAA compliance is too expensive or complicated. But there are several HIPAA-compliant cloud storage for small business options available that are both affordable and user-friendly.
HIPAA-compliant cloud storage for small enterprises includes:
These services allow small clinics and individual practitioners to stay compliant without breaking the bank.
Here are a few key questions to ask before making your choice:
The best HIPAA-compliant cloud storage providers should make compliance seamless while supporting your workflow.
HIPAA-compliant cloud storage is no longer optional, it’s a necessity for healthcare organizations. From large hospitals to local clinics, storing and accessing patient data in the cloud offers unmatched functionality and security.
By choosing HIPAA compliant cloud storage solutions, healthcare professionals can ensure they meet regulatory requirements while providing the best possible care. If you’re still asking: Is cloud storage HIPAA compliant? All you need to remember is that yes, it is possible as long as the right safeguards are in place.
With the right cloud consulting companies as your partner in HIPAA compliance, like Arpatech, you needn’t worry about anything. Get the best cloud consultants for your hospital and ensure loyalty of your patients at all ends.
Yes, Google Cloud Storage can be HIPAA compliant, but you must enter into a Business Associate Agreement (BAA) with Google and configure the services appropriately.
Yes, HIPAA data can be stored in the cloud if the cloud provider offers HIPAA-compliant cloud storage and follows all required safeguards.
Yes, Amazon Web Services (AWS) is HIPAA-eligible. It offers many tools and features to support HIPAA compliance, including encryption, access controls, and the ability to sign a BAA.
Ramsha Khan
May 6, 2025

Healthcare Cloud Migration in UAE: Strategy for a Smoot...
If you’re part of a healthcare organization, you’ve probably heard the buzz around healthcare cloud migration in UAE. Everyone seems to be talking about going “cloud-first,” but what does that mean in the healthcare world? And more importantly; how do you make the transition without disrupting care?
Today, we are here to walk you through healthcare cloud migration and its benefits and challenges in healthcare. It will include a foolproof strategy to help an organization planning to migrate to cloud architecture effectively. Whether you’re an IT person or a healthcare executive or just someone curious about the subject, you will find everything in simple, no-jargon language..
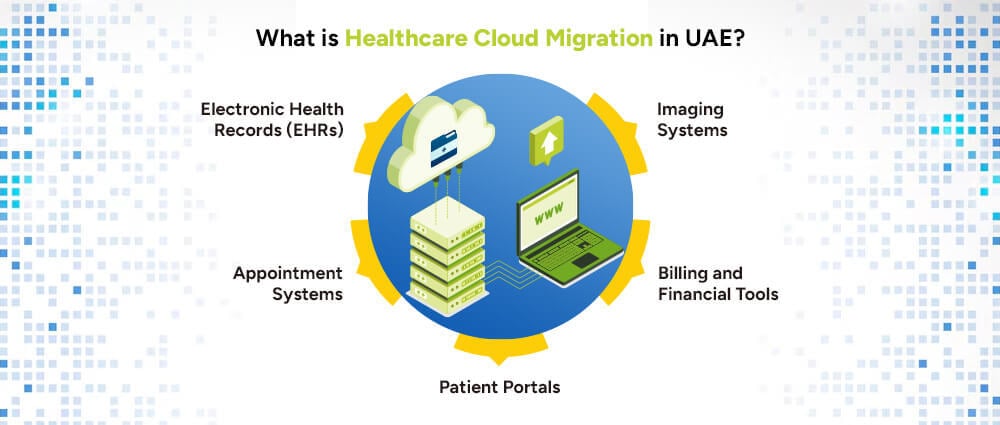
In the rise of cloud-based services for healthcare, the main idea remains the transfer of all data, applications, and processes from physical on-site servers to a properly secured cloud infrastructure. In effect, this means a transfer from the sweatshop of an office into a much smarter, better-managed, scalable, efficient, and accessible virtual workplace. In the cloud space, this is the effortless role of cloud managed services, that act like your movers.
This can include migrating:
Like the economy, the UAE is developing into an increasingly modern healthcare center. Programs such as the UAE Digital Health Strategy 2023-2030 aim to make healthcare more effective, data-driven, and patient-centric. The migration of the hybrid cloud for healthcare in the UAE serves to fulfill this vision via the safe sharing of information, speedy delivery of service, and AI-infused analytical insights.
Here are the 7 benefits of cloud migration for healthcare that are convincing hospitals and clinics across the UAE to make the move:
Doctors, nurses, and staff can access patient information anytime and from anywhere. This makes it easier to make quick and informed decisions. It also supports remote consultations and faster care delivery.
Healthcare providers don’t need to invest in expensive servers or IT infrastructure. With cloud services, you only pay for what you use. This helps reduce overall costs and improves budgeting.
As the hospital grows, cloud resources can easily grow with it. If less capacity is needed, it can also be scaled down. This flexibility helps manage resources without wasting money.
Top cloud providers use strong encryption, cloud cryptography, and multiple layers of protection. They follow strict healthcare regulations to keep data secure. This ensures patient information stays private and safe from threats.
Cloud systems automatically back up data and have recovery plans in place. If there’s an outage or cyberattack, data can be quickly restored. This prevents loss of critical medical records.
Medical teams across departments or cities can share files and updates instantly. This real-time access helps them work together more smoothly. Better collaboration leads to better patient care.
Cloud platforms make it easier to use advanced tools like AI for diagnosis. They also help analyze large volumes of data for trends and planning. This improves healthcare quality and decision-making.
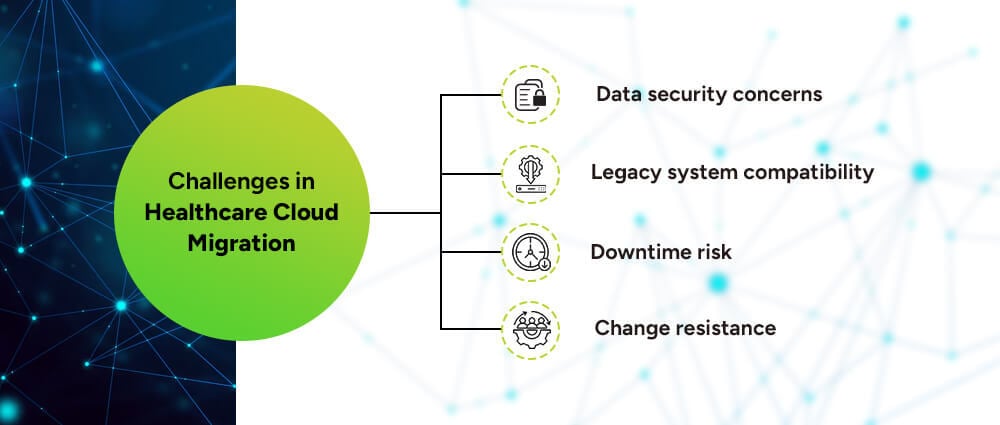
Of course, no transition is without bumps. Here are some common hurdles that companies face when they are thinking to migrate to cloud architecture in healthcare:
Patient data is sensitive and protected by law. You’ll need to ensure full compliance with UAE regulations and international standards.
Old systems may not be cloud-ready, requiring customization or replacement.
If not managed well, migration can lead to temporary service disruptions.
Staff training and support are crucial to get everyone on board.
To ensure a smooth transition, here’s a simplified cloud migration strategy for healthcare providers in the UAE:
there are three steps to access and planning within a healthcare cloud migration platform:
Look for platforms experienced in cloud migration healthcare services like Microsoft Azure, Amazon Web Services (AWS), and Google Cloud are some top names.
Pilot with low-risk applications to test and refine your process before going full-scale.
Work with providers that specialize in healthcare website migration to cloud services to securely transfer data without loss or corruption.
Conduct training sessions for both IT teams and medical staff to get comfortable with the new healthcare cloud systems.
After migration, continuously monitor performance and make necessary improvements.
Cloud migration for healthcare IT is more than simply a technological advancement; it’s a radical change in the way that care is provided. And now is the ideal moment to make the change in a progressive nation like the United Arab Emirates.
You can guarantee a successful, safe, and seamless cloud migration with the correct plan, partners like Arpatech, and assistance, eventually improving the experience for patients and healthcare providers.
Because it offers cloud cost optimization, better data access, enhanced security, and the ability to use AI and analytics for better patient outcomes. It’s all about being faster, safer, and smarter.
Cloud is used for storing electronic health records, telemedicine platforms, managing appointments, medical imaging, billing, and even AI-driven diagnostics. It’s the digital backbone of modern care.
Data migration in healthcare refers to securely transferring patient records, clinical systems, and other digital assets from older systems or on-premise setups to cloud-based solutions.
Popular choices include:
The best one depends on your specific needs and budget. It’s smart to consult cloud consulting companies for healthcare providers before making a decision.
Ramsha Khan
May 1, 2025

Trends in the E-commerce Software Industry in the Middl...
If you’ve been watching the digital space in the Middle East, you’ve probably noticed something huge: the e-commerce industry is at an all-time high. From local startups to big international players entering the market, online shopping is no longer a side hustle. It’s front and center. But what’s really driving this growth? The software behind these online stores.
Let’s take a friendly dive into the e-commerce trends in the software industry and see how things are shaping up across the region.
People in the Middle East are spending more time on their phones than ever before and they’re using them to shop. Mobile-first e-commerce platforms are becoming the norm.
Software developers are focusing on building responsive, fast, and seamless mobile shopping experiences, from personalized product feeds, and e-commerce site with amazing navigation to one-click checkouts. If your e-commerce platform doesn’t work smoothly on mobile, you’re probably missing out on a huge chunk of customers.
One major thing setting the Middle East apart in terms of e-commerce software trends is the need for strong localization. Platforms that support Arabic language, RTL layouts, and local payment gateways (like Mada in Saudi Arabia or Fawry in Egypt) are winning hearts and sales.
Today’s e-commerce software isn’t just about selling; it’s about connecting. And to connect, you need to speak your customer’s language, literally.
Artificial Intelligence (AI) is popping up everywhere in e-commerce, especially in recommendation engines and chatbots. Want to offer a product suggestion that feels like it was handpicked? AI is how you get it.
Retailers in the Middle East are adopting smart algorithms that can track user behavior, shopping history, and even regional trends to deliver a hyper-personalized shopping experience. They also realize the role of voice search assistant in ecommerce to promote accessibility and diversity for their customers.
This is one of the current trends in e-commerce that’s growing fast. People are buying directly from Instagram, TikTok, and Snapchat.
E-commerce platforms in the Middle East are now integrating with social media more deeply, offering “Shop Now” buttons, influencer store links, and even live shopping features. Software that combines e-commerce and social seamlessly? That’s the future. This also enables you to gather social proof for e-commerce sales.

Cash on delivery used to be king, but not anymore. Customers now expect options—credit cards, Apple Pay, STC Pay, BNPL (Buy Now Pay Later), you name it.
E-commerce software must integrate with a variety of payment gateways, and more importantly, keep things secure. With the rise of digital payments comes the need for robust cybersecurity measures, something developers are actively working on in 2025.
Gone are the days of clunky self-hosted stores. Now make way for more businesses preferring to move to flexible, scalable, cloud-based e-commerce solutions that are easier to manage.
Most particularly for small and medium enterprises in the Middle East that want the best enterprise-level applications minus the biting costs or heavy infrastructure.
Online store? Check. Instagram shop? Check. WhatsApp orders? Check.
Modern e-commerce isn’t about having a store, it’s about being everywhere. Software is evolving to help businesses manage inventory, customer service, and marketing across multiple channels without missing a beat.
Yes, even in software! Consumers, especially younger ones, are more conscious about where and how they shop.
Brands are now using e-commerce platforms that highlight sustainability features, from eco-friendly packaging tracking to carbon footprint estimators. Expect more software tools in 2025 that make it easy to sell ethically.
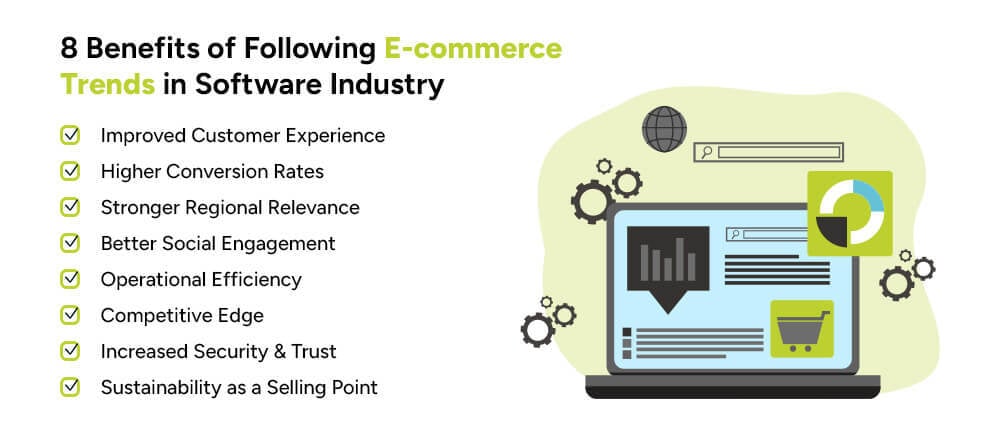
Some key benefits of following the latest trends in the e-commerce software industry, especially for businesses in the Middle East:
Personalized recommendations, faster mobile apps, and localized interfaces (like Arabic support) make shopping more enjoyable.
Happy customers = repeat customers.
AI, smart payment gateways, and one-click checkouts reduce friction in the buying process.
Trends like Buy Now, Pay Later (BNPL) make it easier for customers to say yes.
Following localization trends helps you better connect with Middle Eastern audiences, culturally and linguistically.
You gain trust by offering familiar experiences, like local currencies and payment methods.
By using social commerce tools, you meet your audience where they spend the most time—on Instagram, TikTok, and Snapchat.
This leads to more organic sales and brand visibility.
Cloud-based and omnichannel software solutions help you manage everything from inventory, to orders, and marketing, all in one place.
Saves time, reduces errors, and improves scalability.
Staying updated with the e-commerce trends 2025 puts you ahead of slower-moving competitors.
You appear more innovative and modern to customers.
Adopting the latest cybersecurity measures in e-commerce software protects customer data and your brand’s reputation.
Builds confidence in online transactions.
Leveraging green e-commerce software tools not only helps the planet, it also resonates with eco-conscious consumers.
Adds a unique value proposition to your brand.
Whether you’re a developer, a business owner, or just someone interested in the industry, the trends in the e-commerce software industry in the Middle East are clear: Faster, smarter, more connected, and culturally in-tune.
If you’re planning to start or grow your online store, now’s a great time to explore what the latest e-commerce trends in software industry can do. Contact Arpatech today and work with the best e-commerce software development experts for your business.
The major trends include mobile-first shopping, AI personalization, social commerce, omnichannel experiences, and flexible payments.
Some of the latest trends include:
There are several, including:
The future is all about personalization, automation, and multi-channel presence. AI, AR, and VR are also expected to play a bigger role, along with an increased focus on sustainability and data security.
Ramsha Khan
Apr 24, 2025

Cybersecurity Solutions for Healthcare: Opportunities f...
Like all industries in this world, the healthcare industry in the UAE is in the process of rapid digital transformation. Popularized by technologies such as electronic health records (EHRs), connected medical devices, and cloud-based systems, most medical clinics are now increasingly introducing high-level information technology into their organizations. Such innovations improve efficiencies and patient care; however, they introduce new and very serious cybersecurity risks.
Now, all size medical clinics are very major players in handling a huge volume of sensitive health data. Patient history, insurance details, diagnostic images, and billing information are only a few of the vast amounts of information that have made the health sector a prime target for cybercriminals. In this picture, then, cybersecurity solutions for healthcare should almost be considered mandatory, not optional.
Cyber attacks have evolved, and healthcare organizations have become important targets to cybercriminals as much-sensitive data is processed in these organizations. Patient records contain information such as names, national identification numbers, medical history, and financial data, which can make individuals victims of crimes that arise once this information is misused or sold in black markets.
Cybercriminals often target healthcare institutions because:
These risks are further compounded by the rapid adoption of digital tools and success with big data platforms in the UAE, where the healthcare sector is growing dangerously fast. This makes the need for comprehensive cybersecurity solutions for the healthcare industry, all the more urgent.
Big data is radically transforming healthcare in UAE in its own way: enabling clinics to enhance diagnosis, track patient outcomes, and personalize treatment. However, strong cybersecurity measures are the sentinels for defending this big data migration, which would otherwise be exposed and misused.
These are some issues that medical clinics face on a regular:
Proper protective measures are completely absent when data travels between systems, so a hacker can invade and compromise the transfers. Sensitive patient information is exposed during these transfers.
When every individual in the healthcare organization is granted full access, there is a high risk of accidental and deliberate misuse of data and the need to restrict access only to the specific needful.
Simple password protection cannot do the job anymore. Systems having weak resident login protection can be easily compromised, and patient records are endangered.
Threats can go unnoticed without continuous monitoring, and damage could have already been done. Real-time monitoring helps nip unlawful activity in the bud.
To tackle these risks and issues, healthcare cybersecurity providers should focus on the following strategies to improve cyberattack threats and their malware detection:
Encrypting data from the moment it’s generated till it reaches its end client ensures that the data is unreadable even if it happens to be intercepted en route.
RBAC limits who can view or edit data according to their job function, thereby minimizing the chance of unauthorized access.
These AI and machine learning systems would identify any abnormal behavior or attack prior to causing any harm.
Regular reviews of systems and practices help keep security up to date and ensure compliance with health data regulations.
In the UAE, even small to mid-sized medical clinics must guard against growing digital threats. Thankfully, there are affordable and effective solutions tailored for healthcare settings.
Encrypting patient data, both in storage and while being shared, adds a layer of protection that secures data management against theft and tampering.
These tools act like digital gatekeepers, blocking viruses and preventing unauthorized users from getting into clinic systems.
2FA makes logging in safer by requiring a second form of verification, like a code sent to your phone, along with your password.
Clinics should use protected Wi-Fi with limited access points. A segmented network can keep medical devices and admin systems separate for added security.
Staff should be trained to recognize phishing attempts and other scams. Awareness is key to preventing human errors that lead to breaches.
Frequent backups ensure that data can be quickly restored in case of a ransomware attack or accidental loss, helping clinics get back on track.
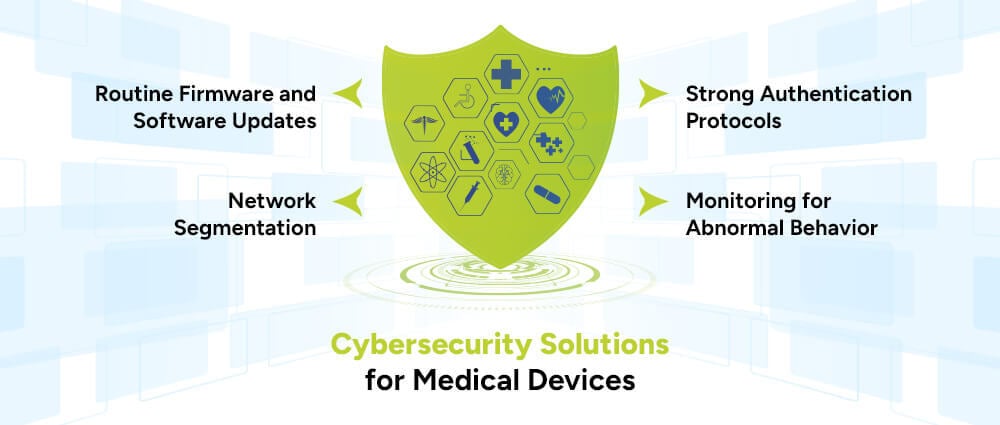
With more smart devices being used in clinics, like ECG machines, insulin pumps, and patient monitors, cybersecurity is required to protect these tools as well from malware and data breaches.
Keeping device software updated closes security loopholes and protects against known vulnerabilities.
Medical devices should require secure logins to prevent unauthorized use, especially when connected to networks.
Separating medical devices from other parts of the clinic’s network helps isolate potential breaches and limits access to critical systems.
Monitoring device activity prevents unauthorized access or weird patterns of behavior from being caught early on and quashing them fast before damages occur.
Well, hospitals can secure patient health and the continued performance of their daily services by securing their medical devices.
One must take a proactive and layered approach to combating cybersecurity threats. Medical clinics should also focus on assessing their vulnerabilities and developing tailored solutions for both technical and human factors.
Steps to improve healthcare IT security include:
UAE is employing robust regulatory frameworks as time goes on and as cyber threats increase. They are serious about protecting patient data at all costs. Medical clinics that follow all of these restrictions and regulations not only avoid penalties but also garner their patients’ trust and build a strong reputation for themselves.
Cybersecurity is more than just a defensive strategy, it is also a growth enabler. By investing in healthcare cybersecurity solutions, medical clinics in the UAE can:
With the UAE’s national push toward smart healthcare, clinics that prioritize security are well-positioned to grow, innovate, and collaborate with both government and private stakeholders.
Cybersecurity is no longer a back-office concern, it is front and center to the success and integrity of modern medical clinics. In the UAE’s rapidly evolving healthcare landscape, adopting robust cybersecurity solutions for healthcare is essential for safeguarding patient trust, ensuring compliance, and unlocking future opportunities.
Medical clinics that prioritize cybersecurity today are building a smarter, safer, and more resilient healthcare system for tomorrow.
Cybersecurity is no longer some back-end support, it has become front and center to the core success and integrity of modern medical clinics. In the rapidly evolving healthcare industry in UAE, putting robust cybersecurity solutions for healthcare in place to enable the safeguarding of patient trust, compliance, and unlocking opportunities. If you are struggling with small data breaches here and there, or are thinking of opening a medical clinic, our recommendation would be to contact a qualified cybersecurity company, like Arpatech, to stop any malware intrusion or data breaches in the future. This way, you can succeed in healthcare and gain your patients’ trust with no hassle!
Medical clinics that focus on cybersecurity today are indeed building a smarter, safer, and more resilient healthcare system for tomorrow.
Cybersecurity in the medical industry refers to protecting healthcare data, systems, and devices from cyber threats. It involves implementing technologies and policies that secure patient records, clinical systems, and connected devices.
The major threats include:
Here are some solutions to use if you want to avoid data breaches in healthcare:
A widely known example is the WannaCry ransomware attack in 2017, which disrupted the UK’s National Health Service (NHS), affecting hospitals, clinics, and emergency services. It highlighted the global importance of securing healthcare systems.
Ramsha Khan
Apr 22, 2025